Some PC owners may need to apply motherboard firmware updates in the near future to address two attacks on TPM chips detailed earlier this month by four researchers from the National Security Research Institute of South Korea.
Both attacks target computers that come equipped with a Trusted Platform Module (TPM). TPMs are dedicated microcontrollers (chips, cryptoprocessors) and they are usually deployed on high-value computers, such as those used in enterprise or government networks, but they are also used on personal computers as well.
The role of a TPM chip is to ensure hardware authenticity. A TPM uses RSA encryption keys to authenticate the hardware components involved in a computer's boot-up process, but also its normal functioning.
The way a TPM works and how the TPM authenticates components part of the boot-up chain is dictated by the TPM 2.0 specification released in 2013.
TPM flaws allow attackers to hide tampered boot components
Two weeks ago, four South Korean researchers detailed two attacks on TPM chips that can allow an attacker to tamper with the boot-up process.
The attacks are possible thanks to power interrupts.
Modern computers do not feed power to all their components allthe time and at the same time. They use special APIs to send power to a component only when it needs it to perform an operation, putting it in a suspended (sleep) state between use states.
TPM chips support ACPI (Advanced Configuration and Power Interface), one of the tools operating systems use to control and optimize power consumption in peripherals.
Researchers discovered two issues affecting the way TPMs enter and recover from these suspended power states, which allow an attacker to reset TPMs and then create a fake boot-up chain of trust for a targeted device.
The first TPM attack
The first attack works against computers which use a TPM chip that uses a static root of trust for measurement (SRTM) system for the boot-up routine.
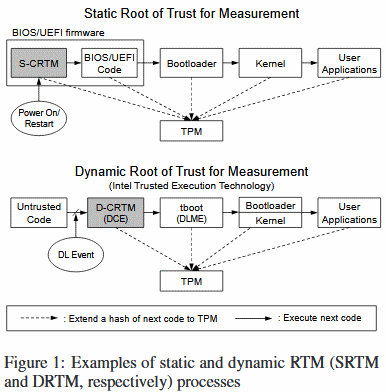
Researchers say this vulnerability is actually a design flaw in the TPM 2.0 specification itself. As nobody spotted the faulty logic until now, the flawed specification was implemented inside TPM components embedded with computers sold by the vast majority of PC vendors.
The attack scenario involves an attacker abusing power interrupts and TPM state restores to obtain valid hashes for components involved in the boot-up process, which the attacker then feeds back to the same SRTM-configured TPM, tricking it into thinking its running on non-tampered components.
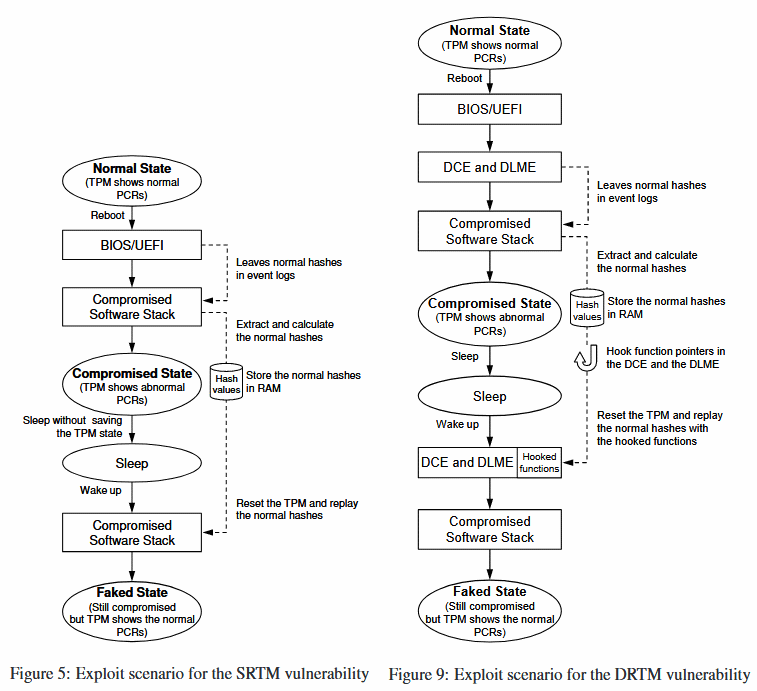
"To remedy the SRTM vulnerability that we found, hardware vendors must patch their BIOS/UEFI firmware," the research team says. "The SRTM attack is significant because its countermeasure requires hardware-specific firmware patches that could take a long time to be applied."
During their experiments, researchers said they managed to tamper with TPMs embedded within computers sold by Intel, Dell, Gigabyte, and ASUS.
"Intel and Dell are in the process of patching their firmware to take corrective action," the research team says. They suspect other PC and motherboard vendors may also be affected.
The second TPM attack
The second TPM attack that the South Korean researchers devised affects TPM chips that use a dynamic root of trust for measurement (DRTM) system for the boot-up routine.
The good news is that this second attack is not as prevalent and wide-reaching as the first. Researchers said this only affects computers running on Intel's Trusted eXecution Technology (TXT) for the boot-up routine.
The actual flaw resides in Trusted Boot (or tboot), an open-source library used by the Intel TXT technology.
Researchers say they contacted the tboot maintainers last year, and provided a patch for the bug, which was incorporated in the main tboot distribution in November 2017.
Be on the lookout for firmware updates
Users interested in rummaging through past or future firmware changelogs for the appropriate fixes can track the two vulnerabilities by their CVE numbers. The SRTM vulnerability has received the CVE-2018-6622 identifier, while the DRTM (tboot) flaw can be tracked under CVE-2017-16837.
The TPM attacks described in this article require physical access to a device, but this doesn't make them less dangerous.
More details about the two TPM attacks are included in a research paper titled "A Bad Dream: Subverting Trusted Platform Module While You Are Sleeping" [1, 2], which was recently presented at the Usenix security conference held two weeks ago in the US.



Comments
gregs_bleeping - 5 years ago
Regarding, "The TPM attacks described in this article require physical access to a device", I don't think that's true. The attacks do require ability to gain root access, but that can be done remotely.