
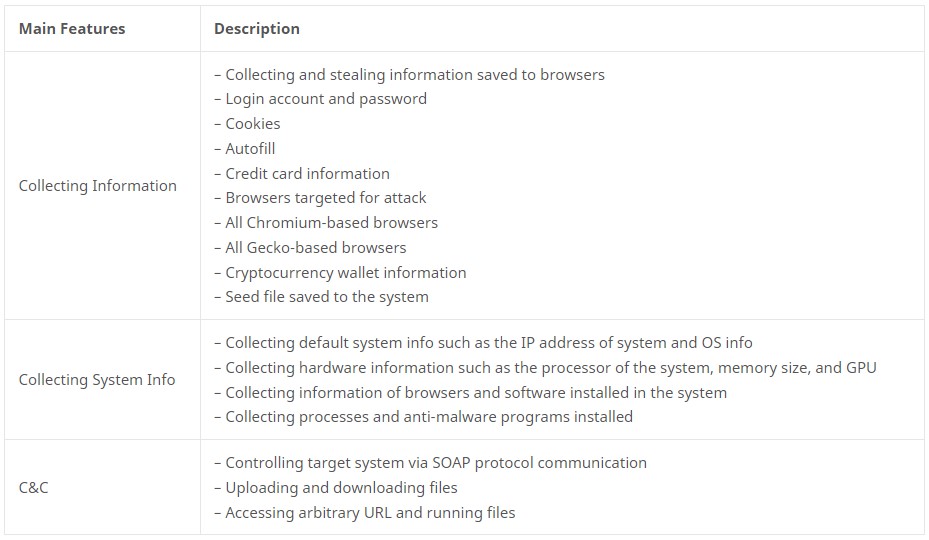
The RedLine information-stealing malware targets popular web browsers such as Chrome, Edge, and Opera, demonstrating why storing your passwords in browsers is a bad idea.
This malware is a commodity information-stealer that can be purchased for roughly $200 on cyber-crime forums and be deployed without requiring much knowledge or effort.
However, a new report by AhnLab ASEC warns that the convenience of using the auto-login feature on web browsers is becoming a substantial security problem affecting both organizations and individuals.
In an example presented by the analysts, a remote employee lost VPN account credentials to RedLine Stealer actors who used the information to hack the company's network three months later.
Even though the infected computer had an anti-malware solution installed, it failed to detect and remove RedLine Stealer.
The malware targets the 'Login Data' file found on all Chromium-based web browsers and is an SQLite database where usernames and passwords are saved.
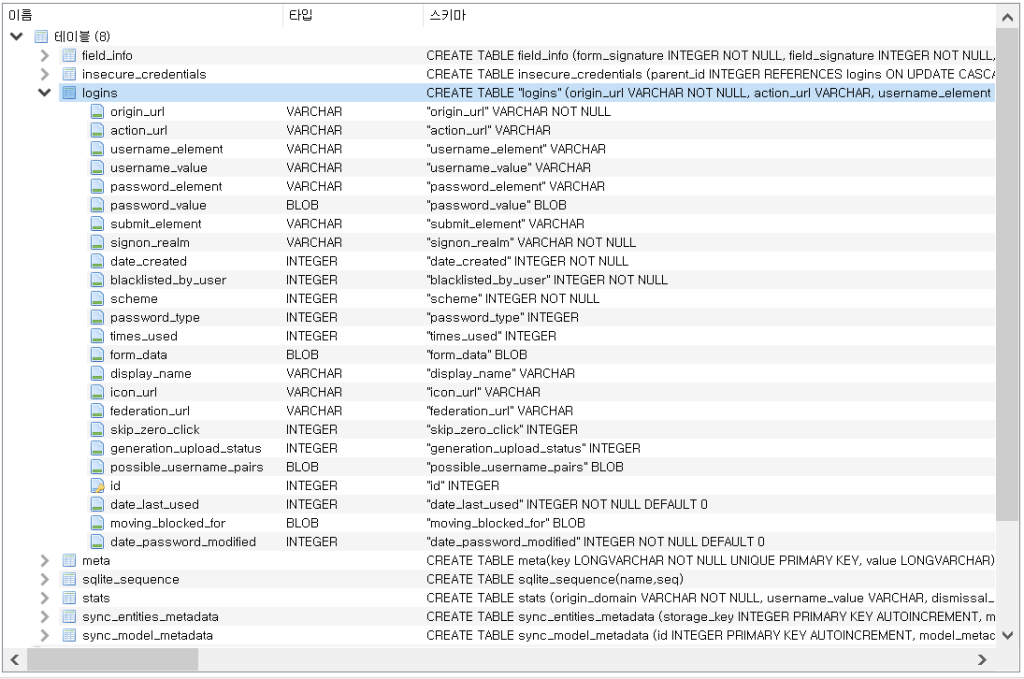
Source: ASEC
While browser password stores are encrypted, such as those used by Chromium-based browsers, information-stealing malware can programatically decrypt the store as long as they are logged in as the same user. As RedLine runs as the user who was infected, it will be able to extract the passwords from their browser profile.
"Google Chrome encrypt the password with the help of CryptProtectData function, built into Windows. Now while this can be a very secure function using a triple-DES algorithm and creating user-specific keys to encrypt the data, it can still be decrypted as long as you are logged into the same account as the user who encrypted it," explains the author of the 'chrome_password_grabber' project.
"The CryptProtectData function has a twin, who does the opposite to it; CryptUnprotectData, which... well you guessed it, decrypts the data. And obviously this is going to be very useful in trying to decrypt the stored passwords."
Even when users refuse to store their credentials on the browser, the password management system will still add an entry to indicate that the particular website is "blacklisted."
While the threat actor may not have the passwords for this "blacklisted" account, it does tell them the account exists, allowing them to perform credential stuffing or social engineering/phishing attacks.
Source: ASEC
After collecting the stolen credentials, threat actors either use them in further attacks or attempt to monetize them by selling them on dark web marketplaces.
An example of how widely popular RedLine has become for hackers is the rise of the '2easy' dark web marketplace, where half of all the sold data sold was stolen using this malware.
Another recent case of RedLine distribution is a website contact form spamming campaign that uses Excel XLL files that download and install the password-stealing malware.
It's like RedLine is everywhere right now, and the main reason behind this is its effectiveness in exploiting a widely-available security gap that modern web browsers refuse to address.
What to do instead
Using your web browser to store your login credentials is tempting and convenient, but doing so is risky even without malware infections.
By doing so, a local or remote actor with access to your machine could steal all your passwords in a matter of minutes.
Instead, it would be best to use a dedicated password manager that stores everything in an encrypted vault and requests the master password to unlock it.
Moreover, you should configure specific rules for sensitive websites such as e-banking portals or corporate asset webpages, requiring manual credential input.
Finally, activate multi-factor authentication wherever this is available, as this additional step can save you from account take-over incidents even if your credentials have been compromised.
Updated 12/29/21: Added more technical details on how passwords can be stolen.
.jpg)

Comments
Gisdude - 2 years ago
This brings me back to my original question: 1. Use a password manager (ie LastPass)? 2. Use browser built in password manager, You can't keep up with this.
Dut - 2 years ago
and password managers are also targeted by malware with scary success rates, what's new?
the worst is having external password manager software that is also masquerading as 2FA
it's gonna take a lot of time to get your digital persona back if something happens (db corruption / ransomware) and eventually you're gonna use the browser anyway to recover from the cloud
built-in password manager in the browser has come a long way, at least that's the case with firefox. I'm sure all of them also feature a master password, cloud saving and etc.
external ones might actually be counter-productive, and their hook/plugin a security issue to the browser in itself
Dominique1 - 2 years ago
I always knew that this feature was trouble, and now I see how easy it is to get to the info. Another thing I hate being saved, especially in the browser, credit card number. :facepalm:
Ascaris5 - 2 years ago
"and the main reason behind this is its effectiveness in exploiting a widely-available security gap that modern web browsers refuse to address."
No... GOOGLE refuses to address it. People have been asking Google for a master password feature forever, and Google's told them "No, you can't have it, so stop asking."
Firefox has the ability to set a master password that can relock instantly or after a user-defined period for years and years. If you use something Google, well...
mrsleep - 2 years ago
""If you use something Google, well..."
And thanks to Chromium that's everything but Firefox now.
dsprg - 2 years ago
I wonder if passwords stored in browsers running on Linux Operating Systems are just as vulnerable.
Googling with that doubt I came here. I see that the author is a Linux enthusiast. Regards.